Summary
On December 17, 2019, Citrix Systems announced a vulnerability of Citrix Application Delivery Controller (ADC) and Citrix Gateway products as CVE-2019-19781. These products are also known as NetScaler ADC and NetScaler Gateway. The vulnerability allows remote attackers to execute a code without authentication. Proof-of-concept (PoC) codes were published on the Internet around January 11, 2020, and we have observed some traffic related to the vulnerability.
Affected Products and Mitigations
According to Citrix Systems, the vulnerability affects following product versions.
- Citrix ADC and Citrix Gateway version 13.0 all supported builds
- Citrix ADC and NetScaler Gateway version 12.1 all supported builds
- Citrix ADC and NetScaler Gateway version 12.0 all supported builds
- Citrix ADC and NetScaler Gateway version 11.1 all supported builds
- Citrix NetScaler ADC and NetScaler Gateway version 10.5 all supported builds
As of January 15, Citrix Systems has not published the patches yet. Citrix Systems indicated that the patches will be released on later this month. Although the patches are not available yet, Citrix Systems released a mitigation instruction. Therefore, users of the product should check the instruction while waiting for the patch to become available.
SOC Measurements
We have observed scan and command execution attack traffic that attempt to utilize the vulnerability. Figure-1 shows the number of attacks and the attack source IP addresses per site.
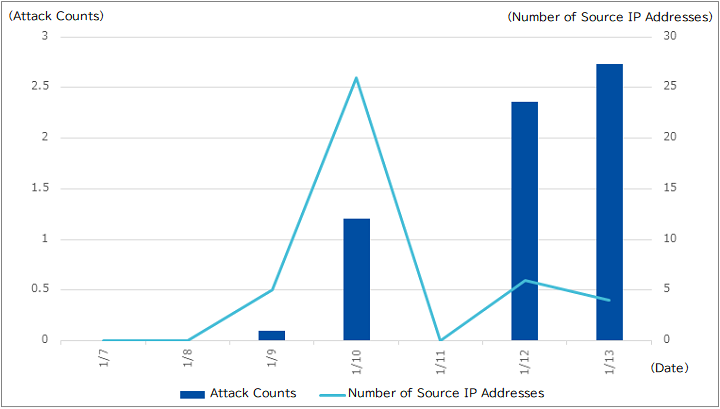
On January 9 and 10, we have observed traffic that attempt to scan for the vulnerability. On January 10, we have observed 26 different source IP addresses for the scans. Figure-2 is an example packet of the scan traffic.

The traffic attempted to access a certain path of the host with a request “GET /vpn/../vpns/”. The mitigation instruction published by Citrix Systems indicated to block accesses to “/vpns/” and “/../” paths. The scan seemed to have searched for appliances that did not have applied the mitigation.
PoC codes were released around January 11. On January 11, we did not observe traffic related to the vulnerability. However, on January 12, we started to detect multiple attack traffic, including attempts for executing operating system commands. Figure-3 is an example packet of the attack traffic.

The request was “POST /vpn/../vpns/portal/scripts/newbm.pl”, and the POST data included “exec(\’uname -a | tee /netscaler/portal/templates/BR257NR5K<snipped>dS9b0vujxZueW.xml\’)”. The command line attempts to redirect outputs of uname command execution, which prints operating system information, to a XML file. The attack might have attempted to: retrieve information from the host, or verify if command execution is possible on the host. In addition to the POST request, we have also observed a GET request to the same host that attempt to obtain the XML file that the command execution might have created.
If your organization have the appliances installed, it is possible that they have already received the attack packets. If you are managing the appliance, verify that the appliance had not returned “200 OK” responses to requests for “/vpns/” and “/../” paths. If there were accesses to Perl files such as “newbm.pl”, please verify that unknown malicious files do not exist on the appliance. Please note that although we have only monitored traffic to “newbm.pl” file, there are reports and tweets indicating that they have observed requests to other Perl file paths.
Conclusion
We have observed traffic that attempt to attack on the CVE-2019-19781 vulnerability of Citrix Application Delivery Controller (ADC) and Citrix Gateway. Citrix Systems have not published update patches yet. We currently have observed scan traffic and attempts to obtain operating system information only, but an article on SANS Diary indicated that there were attacks that attempted to download a backdoor program from the Internet. Please check and apply the mitigation instructions published by Citrix Systems. Lastly, when Citrix Systems releases patches later this month, please apply them appropriately.






